A Beginner’s Guide To Understanding DDoS Attacks & How To Protect Your Site
- Category : Server Administration
- Posted on : Jun 01, 2017
- Views : 1,670
- By : Edgardo D.
As a webmaster, you’ve probably heard the term DDoS and DoS thrown around as a cyber security risk. Although some people throw the terms around interchangeably, they are different types of attacks. Your web host does what it can to defend against an attack, but knowledge is power and it helps your business if you know the signs of an attack and what you can do to defend against it. Maybe you just want some general understanding, and (if that’s the case) this guide is for you.
Basic Web Communication
Before we get into DDoS, let’s first take a look at how web communication works. When you type a URL into your browser, it does a DNS lookup of the domain, finds the IP address, and then makes a call to the domain’s web server asking to access the content. As a webmaster, you probably know the average amount of traffic you get each day. You purchase resources on your server to account for average traffic and ensure that your site is always fast.
During your busy season, you might scale up a bit to account for the increase in traffic. Most webmasters understand that more traffic means that additional server resources are needed.
One common misconception among webmasters is that bandwidth is the same as network speed. It should be noted when discussing DDoS attacks that bandwidth is the amount of data that can be transferred for a given period of time. Think of bandwidth as a water hose. You can only fit so much water in the hose and shoot it from the spigot to the opening. If you need more water transferred during a fixed amount of time, you need to expand the circumference of the hose.
Your web server can only handle so many transactions, and your bandwidth can only fit so much data. These core components are the target of a DDoS attack.
Note: we’re focusing on web servers just for simplicity, but DDoS attacks can happen for numerous services including DNS, DHCP, chat rooms, and even printers.
The Early Days of DoS
A denial of service attack is nothing new on the Internet. Back in the early days of the Internet, one man with one computer could cause a denial of service. As a matter of fact, the first DoS attack was in 1974 and was created by a 13-year old Illinois student.
The days of the early Internet didn’t take much computer power or bandwidth. The resources and bandwidth we have now weren’t even available back then. Having 1000 visitors to your site a month was a lot, and several thousand calls to a web server doesn’t take much computing power.
One of the common DoS attacks in the 1990s as the Internet grew more popular was called a “smurf attack.” The way it worked goes back to the way transmission on the Internet works. When your browser makes a connection to the server, it establishes a “SYN-ACK handshake.”
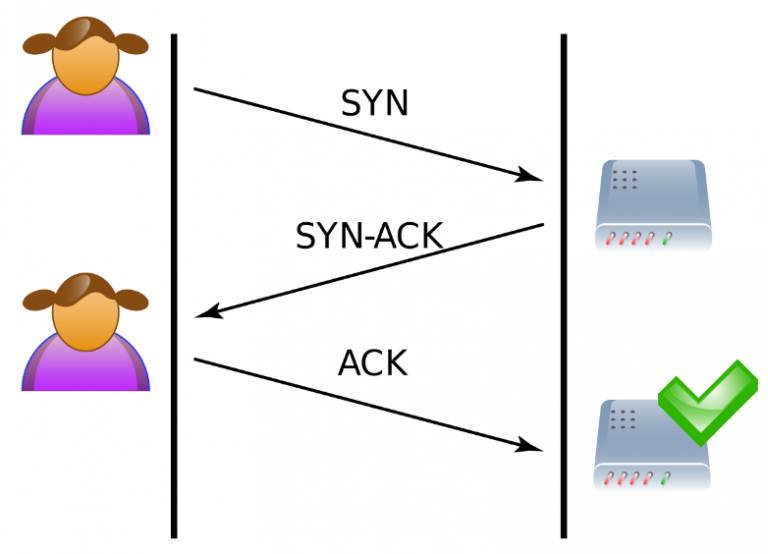
Your browser makes a SYN (synchronize) request to the server. The server receives the request and sends a SYN-ACK (synchronize-acknowledge) message back to your browser. After the SYN-ACK message is sent, the server waits for your response. Your browser then sends another ACK (acknowledge) message back to the server. Both of you establish a connection because both of you synchronized and acknowledged the handshake. You’re both aware that the other exists, and once you make the handshake both you and the server can transfer data.
We’ve highlighted the important part of this process. The server waits for a return ACK from the sender. What happens if the sender disappears or what happens if the sender’s IP address is faked? The SYN-ACK response goes into a dark void and nothing is returned. One or two of these dropped connections are OK, but DoS occurs when there are thousands.
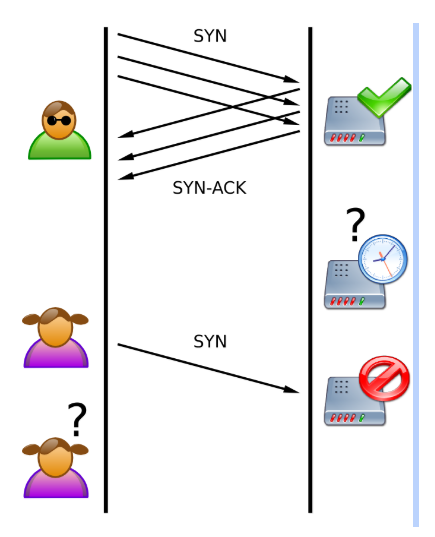
Remember that the server is using resources to wait for a response. With a DoS attack, thousands of these requests are sent and the sender’s IP is spoofed (faked). The SYN-ACK step goes into a void with no hope of a response. The server keeps waiting and waiting as the requests continue to build up. More requests are queued but no response is ever made, leaving the server to continue queuing more and more messages. Eventually, server resources fill and no more resources are available for legitimate requests.
This was the heart of a successful old-school DoS attack. Server resources were exhausted from faked messages that could come from only a handful of computers to be successful.
Moving on To DDoS Attacks
Old school DoS attacks worked great for attackers until server resources were so strong that it could handle what any one computer could send to it. As a matter of fact, the attacker’s computer would crash before the server would crash. The web servers available today wouldn’t skip a beat should a single computer attempt to attack it with thousands of requests. As usual, cyber attackers always find ways around defenses, so they came up with a new way to send a denial of service at a server. We’re talking about a distributed denial of service.
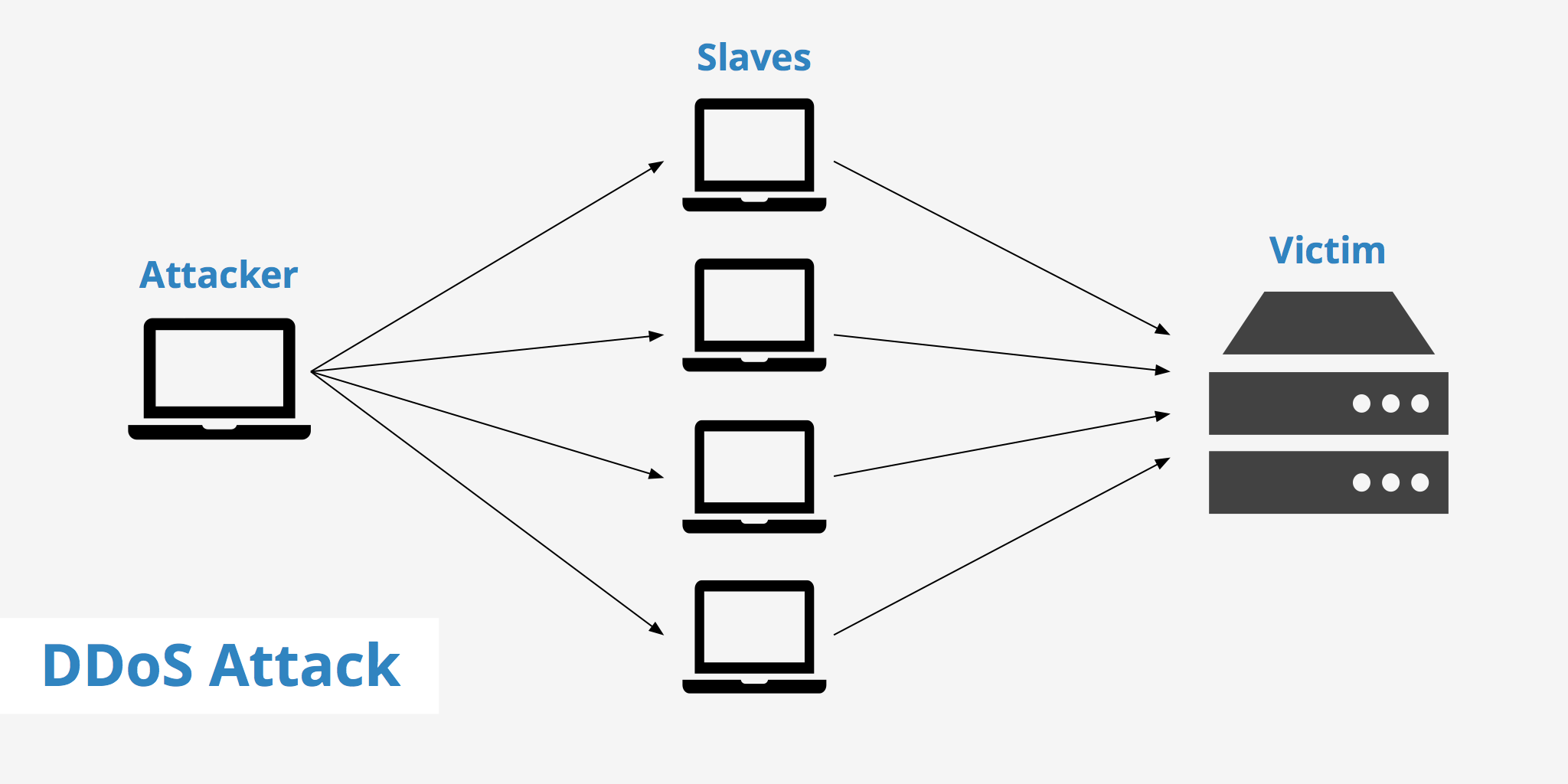
A DDoS works similarly to a DoS, but imagine the requests coming from thousands of computers across the globe. Most standard powerful web servers are made to handle several thousands of people browsing pages each day, but what happens when all 10,000 (for example) hit the server at the same time? The result is that even the most powerful servers have a finite amount of resources, and eventually enough requests cause it to crash.
DDoS is much more complex than a DoS attack. First, the attacker needs more than just a local computer. It takes distribution of malware on thousands of machines that allows the attacker to take control of them. The goal for the attacker is to take control of machines across the globe, so the victim cannot just block one subset of an IP range. Second, the attacker must have a central server application that tells these machines to flood the target’s server with as many ACK requests as possible.
We can go back to server bandwidth being your “hose” for data. The host can only transfer so much data at the same time, and the more data you need transferred, the longer it will take for all requests to go from the spigot (your customers’ browsers) to the server. If too much data floods the server, your customers will receive a timeout error on their computer. The attacker successfully interrupts your business and your sales. DDoS is an effective way for a competitor to destroy your business.
How Do You Know It’s Happening?
Having a competitor destroy your business is a scary proposition. Because a DDoS attack comes from hacked computers across the globe, it’s also difficult to pinpoint when it’s happening. Your first reaction might be “How can I detect one, so I can protect my site?”
Rest assured that host providers have their own DDoS alerts, detection and defense in place. These defenses are generally effective, so you don’t need any type of monitoring. For someone who isn’t technical, the only sign of an attack is severe performance issues on your server. The server might even crash.
If you have the technical know-how to view a list of connections on your server, you’ll notice that you have hundreds or thousands of connections from the same IP range on contiguous port numbers. Your server could even start responding with a 503 error message, which means “service unavailable.”
Your web host will probably know that something is happening before you do, and might even call you. If you reboot the server and you still have performance issues, and you have an unusually high amount of visitors on your site, give your web host a call.
Are There Any Ways to Prevent a DDoS Attack?
Cloud hosting is one way to help with smaller attacks. Another option that’s much more efficient is using proxy services such as CloudFlare. For larger sites that suffer from more collaborated, strategic attacks, enterprise solutions such as Arbor, NSFocus and Staminus are better. These services have a large bandwidth capacity, and they can handle several gigabytes of traffic, filter it and pass only legitimate traffic to your site.
DDoS attacks are also detected on firewalls and routers, but it’s unlikely that you’ll have access to these resources. Your host does, however, and they will be able to help defend against an attack should one occur. Referred to as null routing, the host temporarily brings down your site, changes your IP and re-enables your site for a period of time until the attack stops.
Mitigating DDoS attacks takes some preliminary defense, but it also takes some support from your host. The best way to stop a DDoS attack is to put the right mitigation systems in place before it happens. Here is a summary of what you can do to prevent an attack:
- Use a proxy such as CloudFlare. CloudFlare has a sophisticated system that detects and blocks UDP and ICMP protocols. It also detects SYN/ACK, DNS amplification and Layer 7 attacks. This is sufficient for most small to medium sized attacks.
- If your site is a crucial backbone for your infrastructure and revenue is severely impacted from an attack, you can incorporate more expensive filtering options such as NSFocus, Arbor or Staminus. It costs much more than CloudFlare, but resources are much more secure for high-scale, larger attacks.
- Use a “null route” option. You need access to the infrastructure, so for most clients this option is only used in collaboration with your host. Remember that this option brings the site down temporarily, so you will experience a short-term outage. However, it’s an effective way to mitigate an ongoing attack that consistently affects your site’s uptime and preventative methods aren’t in place.
Categories
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | ||||||
Recent Articles
-

Posted on : Jul 25
-

Posted on : Jul 07
-

Posted on : Apr 07
-

Posted on : Mar 19
Optimized my.cnf configuration for MySQL 8 (on cPanel/WHM servers)
Tags
- layer 7
- tweak
- kill
- process
- sql
- Knowledge
- vpn
- seo vpn
- wireguard
- webmail
- ddos mitigation
- attack
- ddos
- DMARC
- server load
- Development
- nginx
- php-fpm
- cheap vpn
- Hosting Security
- xampp
- Plesk
- cpulimit
- VPS Hosting
- smtp
- smtp relay
- exim
- Comparison
- cpu
- WHM
- mariadb
- encryption
- sysstat
- optimize
- Link Building
- apache
- centos
- Small Business
- VPS
- Error
- SSD Hosting
- Networking
- optimization
- DNS
- mysql
- ubuntu
- Linux